PROTECTING WHAT MATTERS, SECURING WHAT operates, DEFENDING WHAT’S NEXT
Operational Technology Cybersecurity Services
Our Operational Technology (OT) Cybersecurity services are designed to safeguard critical infrastructure and industrial environments against evolving cyber threats. We bring deep expertise in securing complex OT systems across various sectors, ensuring continuous uptime, regulatory compliance, and operational integrity.
Castle Method™ is a structured framework for conducting Cyber Risk Assessments (CRA) and fortifying Operational Technology environments. Developed by cybersecurity thought leader Jamison Chochrek, this methodology prioritizes a holistic and layered defense approach.
Comprehensive Audits
We conduct detailed audits of OT environments to evaluate the current cybersecurity posture. This includes reviewing existing security policies, network architecture, system configurations, and asset inventories to identify gaps and compliance issues.
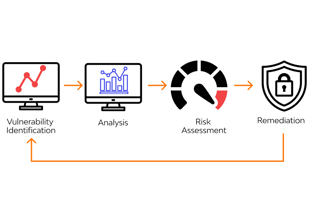
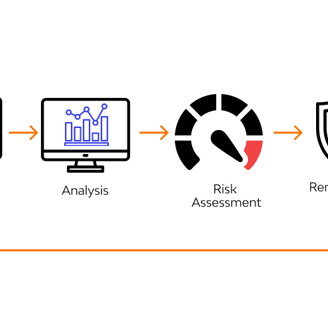
Vulnerability and Risk Assessments
Our risk assessment methodology evaluates potential vulnerabilities within your OT systems and prioritizes remediation based on impact and exploitability. We utilize both automated and manual techniques to uncover latent threats that could compromise safety and reliability.
Penetration Testing
We simulate real-world cyberattacks on your OT infrastructure to test the effectiveness of your existing defenses. Our penetration tests are tailored for OT-specific protocols and devices, identifying weaknesses without disrupting operations.
SCADA Protection
We offer specialized protection for Supervisory Control and Data Acquisition (SCADA) systems, ensuring secure communication, integrity, and authentication between field devices and control centers. This includes segmentation strategies and intrusion detection tailored for SCADA environments.
BACnet/IP Protocol Security
Our team has deep technical knowledge of the BACnet/IP protocol, commonly used in building automation systems. We implement robust measures to secure BACnet communication, mitigating risks of unauthorized access and protocol-based attacks.
DoD Compliance Support
We assist organizations in aligning their OT cybersecurity posture with Department of Defense (DoD) standards and frameworks, including NIST SP 800-82, 800-171, and CMMC requirements. This includes gap analyses, documentation, and roadmap planning to achieve and maintain compliance. For more information on CMMS requirements click the button.
With a focus on resilience, safety, and performance, our OT Cybersecurity services ensure that industrial systems remain protected, compliant, and optimized against the ever-changing cyber threat landscape.