PROTECTING WHAT MATTERS, SECURING WHAT operates, DEFENDING WHAT’S NEXT
Cyber Operations and Resilience Services
Fortify Industrial Infrastructure with Operational-Grade Cyber Resilience
Our services combine cutting-edge threat intelligence, operational discipline, and proven frameworks like the CASTLE Method™ and the SANS ICS 5 Critical Controls. We ensure your industrial control systems are not just secure—but resilient and safe.
CASTLE Methodology Integration
Our services are built on the CASTLE Method™ — a comprehensive OT security framework that encompasses:
Controls: Safeguard ICS protocols (e.g., BACnet, Modbus) and ensure control systems are resilient
Applications: Secure ICS/OT applications, agents, APIs, and HMIs with WAF and hardened OS baselines
Systems: Protect all powered devices—PLCs, RTUs, SCADA servers, switches, IoT/IIoT—from threats and misconfigurations
Threats: Mitigate both insider and outsider threats using ASA (Attack Surface Analysis) and CTL (Cyber Threat Landscape) mapping
Law: Align with legal and regulatory obligations (FTC, GLBA, NIST, IEC 62443, CISA, Tennessee & Florida state laws)
Employees: Minimize human error and insider threats through awareness, training, and access control
Core Services
1. OT-Specific Incident Response
ICS-specific plans and drills using Dragos and CASTLE threat models
Consequence-focused exercises to protect safety-critical processes
Legal-readiness aligned with SEC, GLBA, and other mandates
2. ICS Network Visibility & Threat Monitoring
Passive and active collection using the Dragos Platform and Agent
Monitoring of Layer 1–4 traffic with protocol awareness
Detection of Living-off-the-Land (LOTL) and ransomware behaviors
3. Secure Remote Access
On-demand vendor access with MFA and monitoring
Secure jump-host architecture
Enforced chokepoints and logging per NIST SP 800-82
4. Risk-Based Vulnerability Management
Vulnerability triage using CASTLE threat priorities and Dragos Now/Next/Never
Accurate asset inventories and firmware validation
Integrated with CMMS, EAM, and OT patch governance
5. Defensible Architecture
Implementation of segmentation per Purdue Model + crown jewel defense
Firewalls, DMZs, and microsegmentation design
OT/IT boundary security aligned with IEC 62443-3-3 SR 3.1–3.14
Advanced Capabilities
Threat Hunting: Detect persistent threats using CASTLE Threat + Dragos TTPs
Resilience Workshops: Build continuity strategies based on ICS impact analysis
Compliance Support: Prepare for audits and assessments (e.g., NERC CIP, EPA SDWA, TDEC/DEP compliance)
Cyber Maturity Benchmarking
Utilize Dragos' Maturity Journey (Implement → Operationalize → Optimize):
Assess your standing in each CASTLE domain
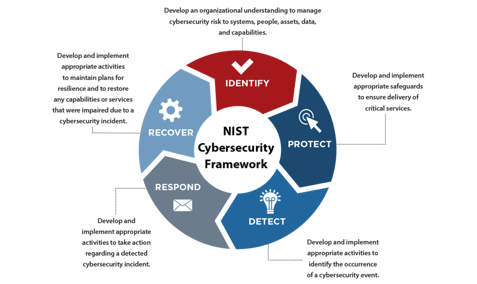
Align security programs with NIST CSF + SANS 5 Critical Controls
Drive continuous improvement and ROI on cybersecurity investments